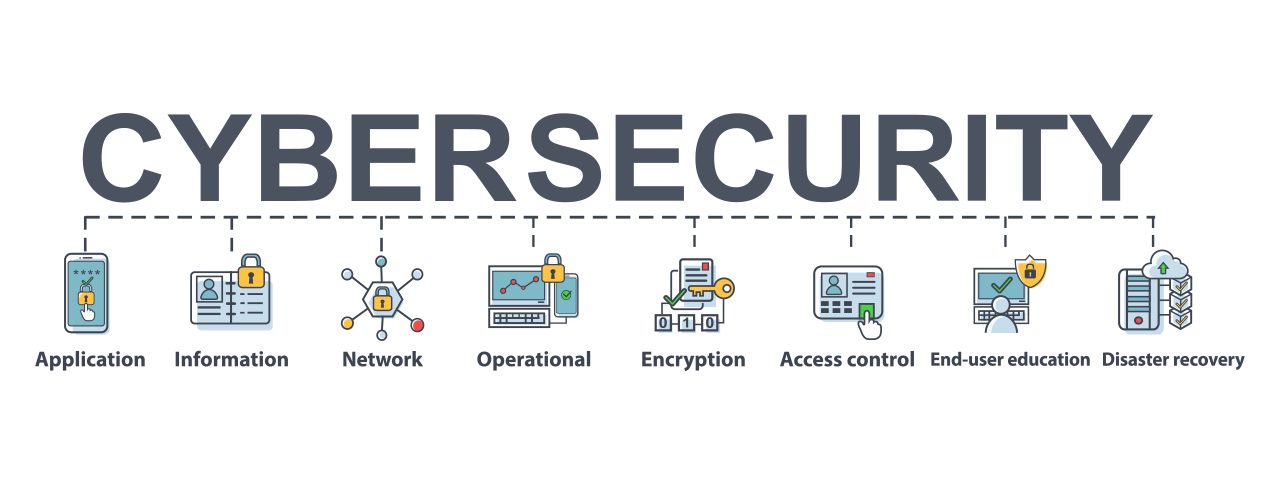
Cyber security solutions are the comprehensive procedures implemented to attain this security and safeguard against typical cyber threats. Cyber security is the term used to describe a company’s protection against the unauthorized or malicious use of electronic devices data.
Cyber security services frequently target the following threats:
Phishing attacks
Cybercriminals use phishing to obtain data by pretending to be legitimate business representatives. They’ll often issue a warning related to your account and ask you for a response with a link to a fake website asking you to provide passwords or other sensitive information.
DDoS attacks (distributed denial of service)
DDoS attacks restrict network access by saturating it with traffic demands that make websites take longer to respond. This is frequently done as a diversion from other forms of cybercrime.
Viruses and malware
A program loaded on a system with the intention of undermining the availability, integrity, or confidentiality of the data is known as malware or malicious software. Despite being covert, types of malware have grown to be one of the major external risks to company networks today.
The ransomware problem
Through the use of software, ransomware restricts access to your own system by encrypting it. To unlock the system and recover access, you are then prompted to pay a “ransom” online.
Cybersecurity uses a variety of network security approaches to block these and other attacks while protecting your data, networks, and systems. Among the several cybersecurity options are the following:
- Data encryption: Data encryption makes sure that criminals wouldn’t be able to view your information even if it were stolen. If you often move data across systems, encryption is extremely crucial since the data may be stolen while being sent.
- Data loss prevention: Data is crucial to your daily operations, and data loss prevention techniques guarantee that your data is always accessible to you.
- Access control: Only a select few employees in your firm should have access to confidential data. Access and identity management make sure that only those with a need to know may access data and that those accessing it are who they claim to be.
- Firewalls: To protect against malicious attacks and unreliable networks, firewalls control the flow of incoming and outgoing network traffic.
- Solutions for anti-virus and anti-malware: Antivirus and anti-malware software is one of the most crucial cybersecurity solutions for any computer network. Viruses are kept out of your devices and the system is examined for threats.
- Web filtering: Web filtering keeps employees from inadvertently utilizing risky services that might expose the organization to network data breaches.
- Risk and compliance management: Organizations in a variety of industries need cybersecurity services in order to adhere to legal requirements or professional norms. Risk and compliance management provides a targeted method to meet these needs.
Cyber security Solutions Solve a Variety of Problems
Businesses of all sizes and types deal with a multitude of possible security problems every day. Cyber security solutions can eliminate problems like these:
- Employee error: Rather than malevolent intent is by far the main cause of data breaches. By preventing employees from visiting dangerous websites and falling for phishing scams, web filtering and other cybersecurity measures reduce the risk of human error.
- External threats: Hackers are getting better at figuring out how to get past conventional firewalls and steal your data. Through cybersecurity services, you can be confident that your firewalls, antivirus programs, and other solutions are always current and prepared to defend your infrastructure.
- Insider crime: Unfortunately, data theft from within a company is one of the most difficult realities for both small and large enterprises. Security measures protect your data from the inside out, ensuring that only those with a need to know may access your sensitive information.
- Unsecured cloud storage: As cloud servers become more and more common, so too are security flaws in cloud storage on the rise. Network security services guarantee that your cloud systems are secure enough to prevent data intrusions.
- Security of third-party apps: Not all applications are developed with the security of your business in mind. Many third-party programs don’t provide enough security features or ones that can be updated. Cybersecurity eliminates these risky applications and implements the security controls that many apps are missing.
- Poor IT processes: Small firms can lack the resources or expertise necessary to keep up with evolving security best practices or rising risks. Many businesses inadvertently put their infrastructure in danger because they lack the funds to engage a professional IT team.
There are several types of IT security solutions
Small and big enterprises have the opportunity to adopt IT security at a scale and budget that’s suited for them thanks to three primary categories of cybersecurity solutions:
- In-house: To provide cybersecurity services, many sizable firms have their own security team in place. With personnel that is familiar with your company and its unique requirements, this do-it-yourself strategy enables you to take charge of your own security and privacy.
- Outsourced: Having cybersecurity managed by a third-party team is a great method for organizations to spend less time on time-consuming security procedures and more time on more productive duties.
- IT security as solutions: Using IT security as a fix In the era of software as a service (SaaS), more goods and services, including cybersecurity, are now accessible via the cloud. Cybersecurity An outsourced strategy known as SaaS involves paying for cybersecurity solutions on a subscription basis.









Discussion about this post